


At Galvanize, we take security seriously.
Every person, team, and organization using our service expects their data to be secure, available, and handled according to strict confidentiality and privacy principles at all times—and we understand how important this is.
We have built our global business on the trust our customers place in our ability to safeguard their data, and continue to maintain that trust through our security and compliance initiatives and culture of continuous improvement.
We are committed to providing a robust and secure service that protects our customers' data.
We provide our service to customers and we also use it ourselves—storing our corporate data in our products. We do so knowing that our platform is built upon industry-leading security technology, refined principles and practices, and ongoing investments in security training, testing, independent audits, expert consulting, and advanced tooling.
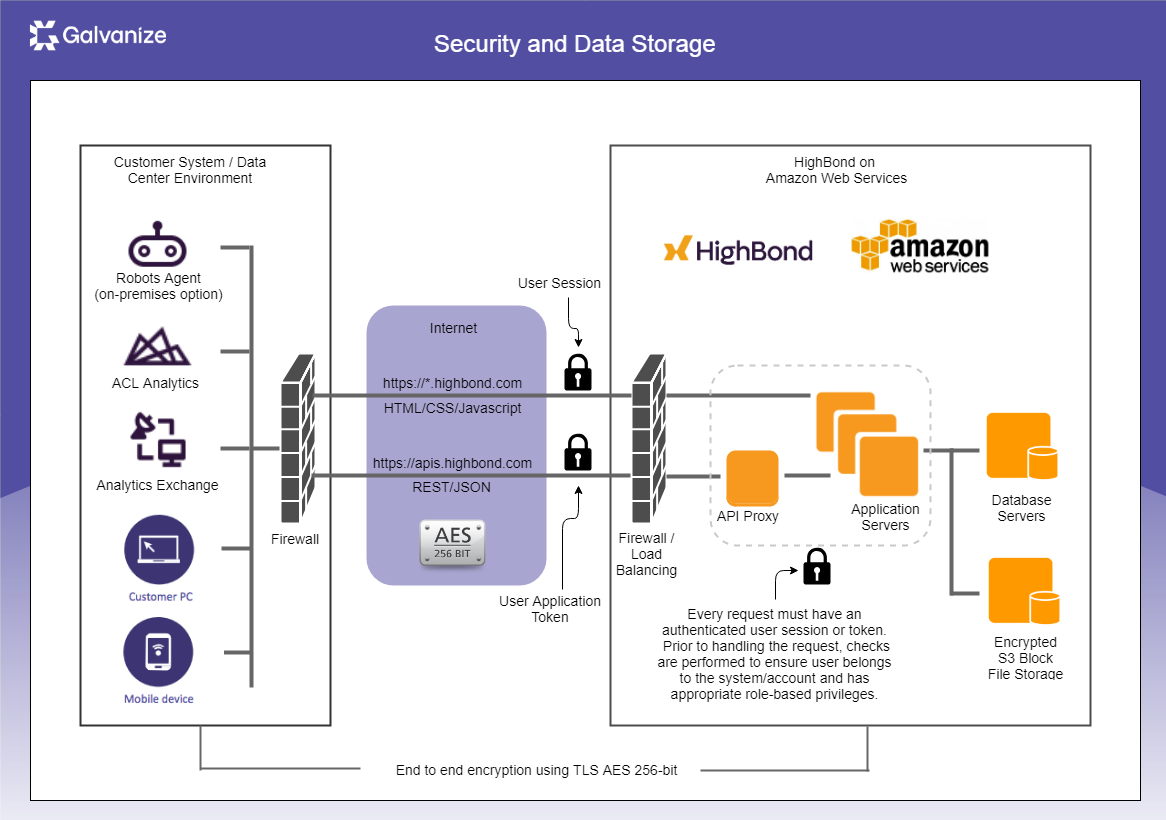
We provide a multi-layered security environment following the principles of least privilege, separation of duties, defense in depth, and usability. Customers have full ownership of user access controls and manage the entire customer data life cycle in deciding:
Our service is hosted by Amazon Web Services, a widely recognized and industry leading cloud infrastructure vendor, and takes advantage of the security infrastructure and benefits provided by Amazon. Within the hosted environment, our customers are provided with their own application environment (your Galvanize service).
We manage the overall application infrastructure and our customers manage the end-user security and access control to own application environment. For more information, see Policies & Processes.
Our service is designed to take advantage of the efficiency and accessibility of a cloud-based, software as a service (SaaS) delivery model. Our SaaS solution provides organizations with independence and agility along with a low and predictable total cost of ownership.
Our service is designed with the philosophy of “convention over customization,” enabling our customers to immediately leverage configurable “out of the box” functionality vs. relying on heavy customization, complexity, and the overhead costs it brings. Time to value with a SaaS delivery model is significantly lower than with on-premise solutions. This means that implementation times are typically measured in days vs. weeks or months for other solutions.
Our service is enhanced with robust best practices functionality, and product improvements are delivered on a continuous delivery basis so you don’t need to wait for long release cycles or internal IT resources to use the latest product version. This ensures that the user interface and product features remain modern and up-to-date with business demands.
The SaaS delivery model takes away large upfront capital or implementation costs, making the ongoing costs much lower and more predictable than legacy on-premise alternatives.
Our service does not require new hardware, software, or IT support for initial implementation or ongoing maintenance. Our customers can self-manage and focus on using the application for their business function, leaving the complexities of administrative management, application operation, and maintenance of the infrastructure to our global operations team.
Our service was designed with usability as our number one priority. Its elegant, interactive, web-based interface means that organizations can start using it quickly.
Our products integrate seamlessly, providing an end-to-end technology solution for audit, compliance, finance, IT, and risk management from a single vendor.
Our service is easily and immediately accessible to employees spread across multiple locations worldwide from their PC, smartphone, or tablet.
We use industry advanced and mature infrastructure-as-a-service (IaaS) providers to host our SaaS offering from global data center locations. The data centers provide many physical and logical security controls and are compliant with various certifications and third-party attestations, including but not limited to: ISO 27001, PCI DSS Level 1, SSAE-16/ISAE 3402 SOC 1 (previously SAS 70 Type II), SOC 2 & 3, and HIPAA. Below are examples of these controls:
These controls ensure facility and equipment safeguards for areas such as multi-factor access controls, electronic surveillance, intrusion detection systems and environmental safeguards.
We review the certifications and third-party attestations provided by our sub service providers on an on-going basis to attest the services being provided and supplement complementary elements to our internal controls.
Yes, we have a current SOC 2 report prepared by a third-party auditor. This report is a comprehensive assessment of the internal controls and information security related to our service.
Upon request and subject to customer’s execution of our standard non-disclosure agreement (NDA), we will provide a copy of its current SOC 2 report.
Besides being the top cloud infrastructure vendor globally, AWS is also a highly audited entity and has many 3rd party reports and attestations.
To access the SOC reports, click here.
For additional information regarding AWS security, click here.
To access the AWS services compliance roadmap, click here.
If you would like to obtain any of the AWS compliance reports, especially their SOC 2, please request instructions from your Galvanize account executive.
Note
Based on the standard agreement all SaaS vendors have with Amazon, we cannot provide these reports directly to you. However, we will help you with information as to how to obtain them directly from Amazon.
In addition to internal security testing, we use third-party independent penetration testing to check our service for security vulnerabilities. These tests are performed by an organization specializing in software security, and are used to probe our environment for vulnerabilities, such as:
We ensure exploitable vulnerabilities are resolved in a timely basis based on severity and impact. Subject to an NDA, we can provide a copy of the most recent penetration test.
Our system control environment is designed to provide confidentiality, availability, and integrity for our SaaS offering. Controls that are semi-annually audited under SSAE-16 include:
These controls and their supporting policies provide us and our customers with operational assurance.
For more information, see Policies & Processes.
Our system is provided from five regions in the United States, Canada, Europe, Australia, and Asia in order to provide our customers with options where their data is stored. These options enable our customers to comply with data privacy location requirements.
PII is limited by our customer subscription agreements, sub service organization agreements, corresponding controls, and segregation built into our SaaS design. This ensures that any PII is isolated and protected in the system and that each customer has access to its data only.
You will continue to retain all rights over your data and we will not use your data except for the purpose of providing the service you have subscribed to.
We recognize that the decision to store data in a cloud-based platform raises important questions about security.
We also know that our 14,000 customers globally have data security and privacy as their top concern. If you have any questions or concerns about the security, privacy, or integrity of your data, contact our support team.
See our Vulnerability Disclosure Policy
To check the real-time performance of our service, visit status.highbond.com.
You can also choose to receive status notifications by subscribing to email updates from our status page.
Our products are governed by the end-user license agreement and/or terms of use that accompany the product.
For more information, see Galvanize Legal.