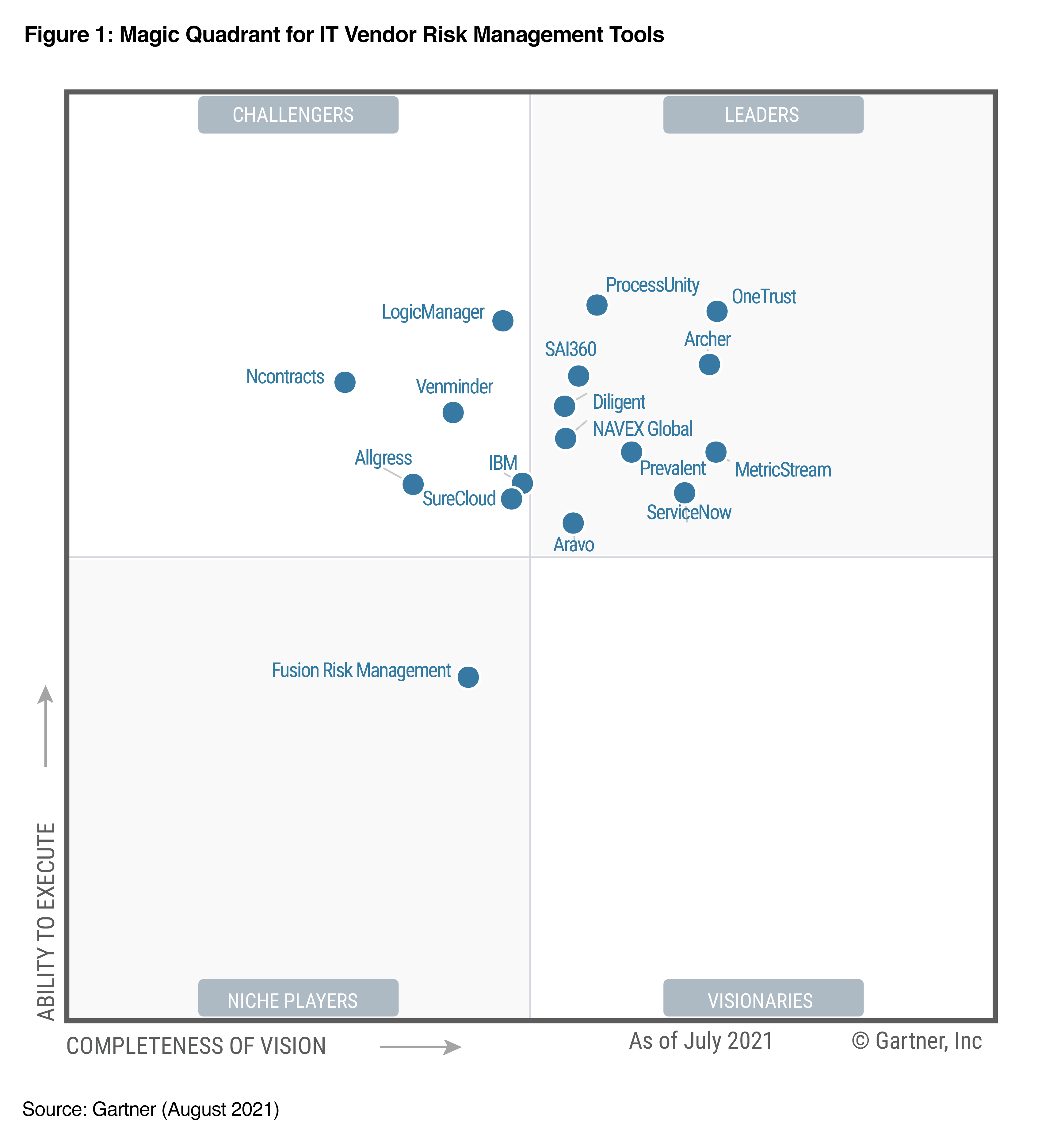
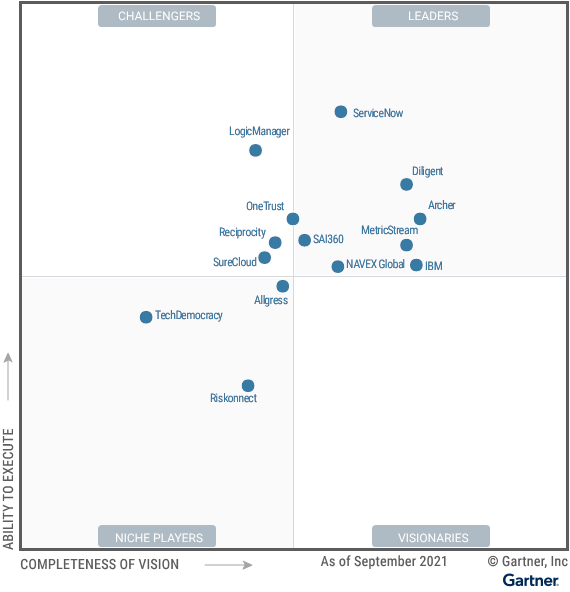
Cybersecurity is a top concern for all areas of an organization, from legal to HR to IT to operations.
A data breach can be devastating, not solely for your technical team, but for the entire company—and can have lasting repercussions. Depending on the severity of the breach, you may need to shut down operations completely for a period of time, which can also lead to customer and revenue loss.
Reputational damage is also a key concern—65% of victims of a data breach have lost trust in the organization that was breached. And companies that inadvertently expose personal information may be subject to class-action lawsuits to the tune of millions of dollars. In terms of financial fall-out, the average cost of a data breach in the United States is nearly $4 million.
Compliance with industry regulations is a good starting point for defending your organization. But now, relying on compliance alone is no longer enough. It’s not about ticking a box, it’s about being aware of, and constantly surveying new and emerging risks, managing existing risks, and making that process efficient. That means it’s essential to take an active approach to monitoring and managing your cyber risk.
Case in point? The COVID-19 pandemic brought on a sudden and widespread migration to a distributed office environment with minimal time to prepare or set up new network security protocols. This resulted in a security breach in 20% of organizations surveyed.
This is a prime example of a risk that could be identified early on. The risk might not have been a global pandemic, but perhaps one of business continuity—if the workplace becomes inaccessible for whatever reason, are the right systems, tools, and processes in place to carry on? If not, how will that affect the organization? This is an example of taking a risk-based approach to cybersecurity.
In order to stay a step ahead of future cybersecurity risks, it’s important to take a strategic approach to assessing potential risks to your organization (including internal, third-party, infrastructure-based, and Act of God scenarios). By identifying each individual risk and building plans for mitigating and remediating them, you’ll be well-prepared to recover quickly in almost any scenario.
A risk-based approach to cybersecurity
Here are five steps for building risk management into your cybersecurity initiatives:
- Use risk scoring and analytics
Take inventory of all of your potential risks, and give them a risk score of high, medium, or low. Then define what level of risk you’re willing to assume, and how much you’re willing to invest to mitigate risks outside of that level. Use a software platform with data analytics to apply and monitor your risk scoring, and automate notifications for when risk trends in an undesirable direction. This article outlines the eight steps that you can use to help plan your cyber risk assessment.
- Create a cyber risk committee
Identify risk owners across the organization. Typically, the Chief Information Security Officer (CISO) will serve in a leadership function for managing cyber risk as a whole, with different teams and job functions playing a role in monitoring and managing specific risks. For instance, IT may take primary responsibility for managing and monitoring infrastructure and networks, while your security team may take the lead on setting controls for accessing data and monitoring threats against it. Group key leaders from each relevant department to serve on a cyber risk committee that reports to your board of directors. This committee should not only monitor active risks, but take responsibility for evaluating the cybersecurity program’s ongoing needs, and allocating resources and updating policies in line with your organization’s objectives.
- Take a phased approach
Rather than trying to implement several major strategic changes at once, take a phased approach to risk management, based on your available budget and resources. Work with the risk management committee to understand the risk landscape, and follow their priority list to help you create a strategic roadmap for addressing risk, including the timeframe at which change will be implemented. This will help define the resources (people, technology, process) you need to implement change over time.
- Put the spotlight on your cybersecurity initiatives
Once you’ve developed a comprehensive cybersecurity risk management plan, educate your entire company about your initiatives. Start by making updates to your policies reflecting changes to standard protocols, and run departmental training programs to get each team up to speed on what they’ll be asked to do. Once your company is on board, you can spread the word by showcasing your cybersecurity initiatives to your clients and partners, providing a competitive advantage. Your reporting analytics will help you here: By focusing on data points such as the speed of risk reduction, you’ll be able to demonstrate to both your board and to external partners and customers that your cybersecurity risk management efforts have made a substantial impact through the organization.
- Identify the right automation tools to help you manage risk
Cyber risk management will benefit from human expertise, but in order to build a robust program that closely tracks your risk level in real time, it will be necessary to rely on automation and data analytics tools. When choosing a solution, focus on finding a tool that will be intuitive to users without specialized training, so that it can be used across lines of business. The tool should use real-time data feeds to analyze new threats, and anonymously share information as incidents and threats occur. It should provide investment v. impact figures for helping you understand your ROI on each mitigation strategy.
By shifting away from a compliance focus and building a cybersecurity plan that’s focused around your company’s unique risk profile, you’ll be in a strong position to effectively and efficiently detect and respond to any threats as soon as they occur, rather than months later.
This will help your business avoid the operational problems and reputational damage caused by major breaches, and remain competitive in your industry for the long run. By using technology that helps you not only assess risks, but also analyze the costs associated with mitigating them, you can run a cost-effective risk management program that gets results.
eBook:
CISOs in the boardroom
In this eBook, you’ll discover:
- The top six challenges facing CISOs today.
- What’s defining our current cyber-risk landscape.
- Strategies to win more budget and capacity for your cybersecurity function.
- Common questions to anticipate from the board (and how to respond to them).