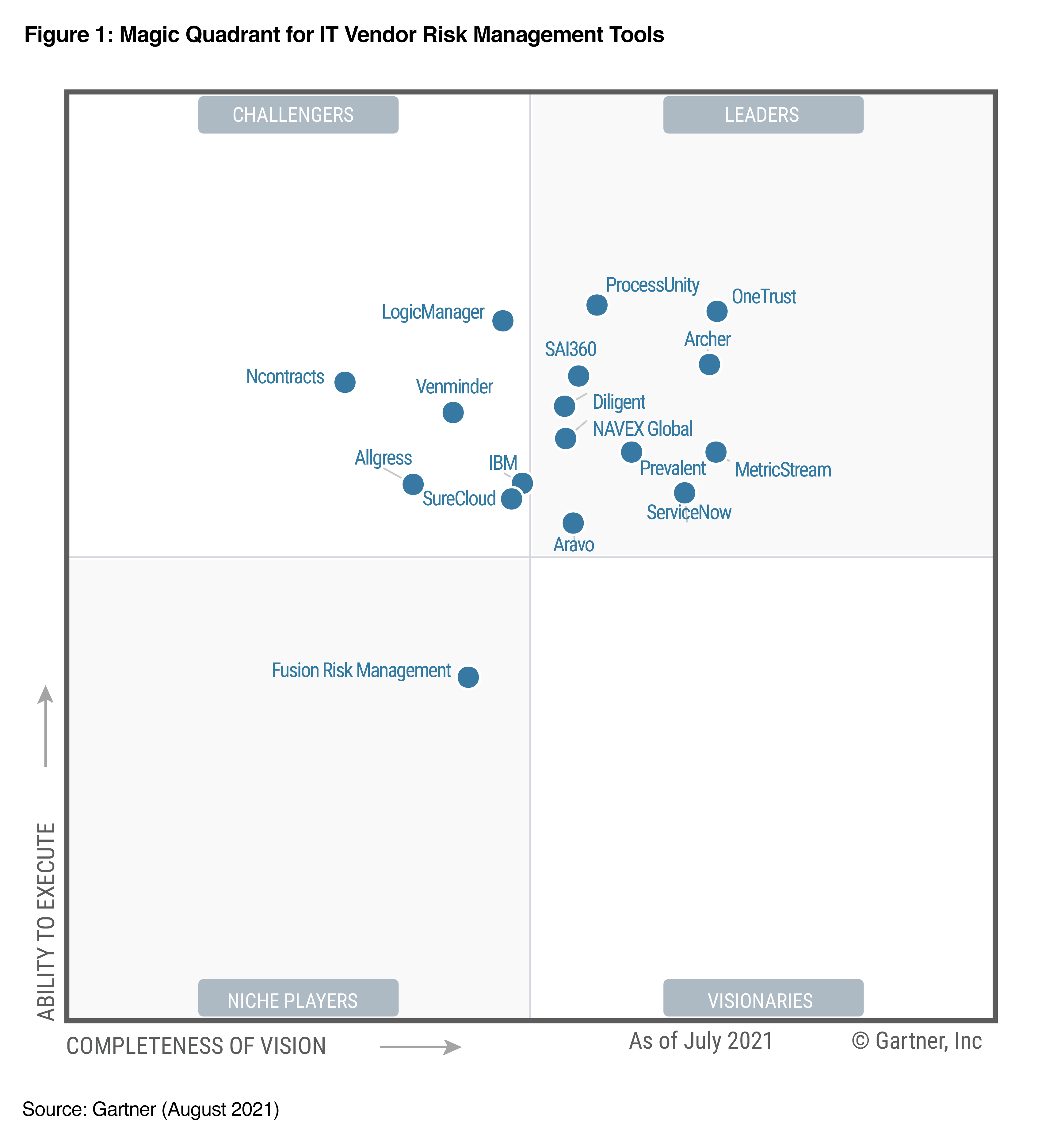
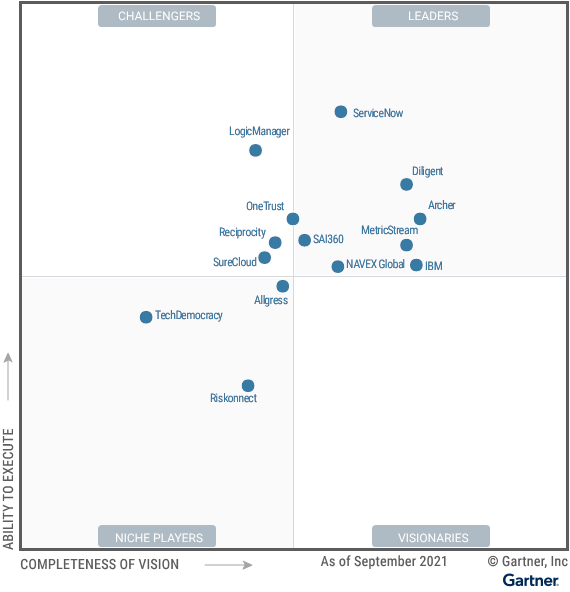
Most organizations have now realized the critical importance of cybersecurity risk management.
On average, it costs $3.86 million to deal with the fallout from a data breach, and it takes an average of 280 days to identify and contain a breach. For an enterprise organization, the cost can be far higher: Capital One, for instance, estimates its 2019 losses from a data breach to be as much as $150 million.
Even without experiencing losses from an actual breach, there’s still the time and cost involved in complying with strict industry regulations for data and privacy protection. Additionally, organizations that do business within the European Union are subject to the EU’s General Data Protection Regulation (GDPR), which can impose fines of up to €20 million (about $24 million) or 4% of annual global turnover.
Given the risk of an actual breach plus the danger of being fined for falling afoul of regulations, many organizations have prioritized cybersecurity as a core concern of their risk management program, which typically falls under the domain of the Chief Information Security Officer (CISO). But cybersecurity risk management programs can vary in terms of goals: some are focused solely on meeting compliance objectives, while others focus on mitigating actual cybersecurity risks.
Organizations that focus on compliance alone are overlooking substantial risk factors. While setting up a good defense posture can help mitigate many known threats, it means that you lack visibility into the changing threat landscape, so you may not be prepared for many scenarios that may arise. In the case of the COVID-19 pandemic, for instance, a huge number of organizations were caught unaware and found their security compromised as their teams moved to remote work without adequate infrastructure or preparation, opening up the organization to risks of fraud and data breaches. In Q1 of 2020, large-scale data breaches occurred at a pace nearly 300% above the previous quarter.
In order to better prepare for changing risk scenarios, it’s essential to build a cybersecurity approach that’s focused on risk evaluation and management, not just compliance. Here are some best practices for getting started.
- Implement a steering committee
Build a cross-disciplinary steering committee to help you report your risks across the organization, collaborating to determine which ones are the highest priority to address. - Balance your goals between aspirational and achievable
As you put plans in place, make sure you’re focusing on objectives that aren’t so pie-in-the-sky that they’ll never be accomplished. A good rule of thumb is to consider only plans that could be implemented within the space of two years. - Grant your organization a grace period
New policies and technologies can’t be implemented instantly; give your organization time to research options and ensure a focus on implementation and education. - Focus on mission-critical systems and data assets
Conduct triage, using an impact assessment to assess the criticality of each impacted system or asset from a business standpoint when determining what risks to prioritize. - Evaluate GRC products to help streamline the process
By choosing the right technology stack for your GRC initiatives, you can semi-automate the cyber risk process, which will allow you to maximize staff utilization on more strategic tasks. - Present the business argument to help establish a cyber risk approach
Share a clear and dedicated plan with your stakeholders to improve your business’s cybersecurity posture, including target investment, quick wins, and best practices. - Establish a phased approach
Don’t attempt to “boil the ocean” by doing everything at once. Start with high-priority initiatives and grow your program from there. - Extrapolate the risk insights to other areas of your security program
Once your risk management program is in place, showcase the messaging through policy updates and a company-wide awareness and education program. - Promote the approach to your clients and partners
By showcasing your strategic approach to cybersecurity, you can help improve your company’s competitive positioning.
In the business risk assessment process, take these steps:
- Create a profile: Start by setting up your business profile with an inventory of risks.
- Determine business impact: What financial or reputational impact would each risk have on your business?
- Assess threats: How likely is each threat to occur, based on historical data and industry data?
- Assess vulnerabilities: What weak points currently exist in your organization?
- Determine risk: Assess which risks are the highest priority.
- Treat the risk: Based on the cost and potential impact, should you mitigate, avoid, transfer, or accept each risk?
Keep in mind that cyber risk shouldn’t be silo-based. Other departments will often need training and education around addressing cybersecurity concerns. For example, your HR department should implement policies around avoiding insider attacks, your awareness and corporate education team should develop a seminar on preventing social engineering attacks, and your supplier agreements should include appropriate language and minimum standards to lessen the risk of a third-party breach.
By ensuring you’ve built a comprehensive program that aligns with cybersecurity risk analysis best practices, you can generate buy-in throughout the organization and raise awareness of the importance of the work your team is doing.
For more information on shifting cybersecurity from a compliance to a risk focus, download our eBook.
eBook:
Shifting cybersecurity from a compliance to a risk focus
CISOs need to start taking a risk-based approach instead of only focusing on compliance. This eBook explores:
- What “good” looks like for cyber risk management
- Six steps in the business risk assessment process
- The important role of automation in cyber risk management